解题情况
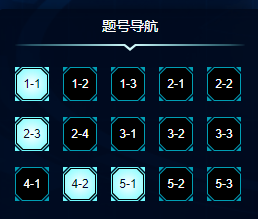
解题过程
Web
1-1 目录扫描
按照经验,猜测robots.txt文件。读取后发现提示'/Sec3et_in_h3r3/fl6g

读取后发现flag。
MISC
2-3 0101
打开文本发现16进制数,用winhex写入,然后根据附件开头50 4B 03 04 14 00 00 00 00 00 判断文件为zip,且文件头损坏而打不开,因此修改为50 4B 03 04 14 00 00 00 08 00.在打开压缩包解压。发现一组黑白图片。编写脚本将黑色图片识别为1,将白色图片识别为0,将得到的二进制数转为字符从而得到flag
识别脚本如下:
1 | #!/usr/bin/env python |
REVERSE
4-1 simple dispy
跟着文档手搓python字节码。大致还原python 源代码为:
1 | arr=[47378,29475,46200,39869,67243,68695,73129,27171,53832,30653,60541,67276,58816,63571,50131,34471,67922,82293,33259,67538,57810,50339,34632,68754,83192,36077,60424,54547,56308,33565,69425,84024] |
从而逆向写出脚本:
1 | #!/usr/bin/env python |
PWN
5-1 ez_canary
1 | [*] '/home/lexs/Desktop/pwntest/2022/cy/ez_canary/ez_canary' |
题目开了canary 和 nx,但是没开PIE.
但是通过逆向源代码和动态gdb,可以得知我们的输入的Username可以溢出到栈上,我们输入的password 可以覆盖 Username的同时溢出到栈上。因此,我们合理布局code让Username 刚好把canary低位的’\x00’覆盖,从而泄露出canary。由于PIE未开,我们可以源文件后门,从而在Password 输入合理布局覆盖Username和canary,让程序流跳到我们后门上。(远程不知道为啥打不通,后赖用 ret 调节下栈 )
1 | #!/usr/bin/env python |
